About Me
Yutaka OIWA, Ph. D.

Deputy Director
and Team Leader for Continuum Computing Trustworthiness Research Team
Digital Architecture Research Center
National Institute of Advanced Industrial Science and Technology (AIST)
Specialty
- Computer System Security
- Software Science and Engineering
- Programming Language (Theory, Design and Implementation)
- Network Protocol and Architecture
Research History
News
-
Machine Learning Quality Management Guideline is published. (Feb 2021)
-
New page AIQA project (1 Dec 2018)
-
New page for distributed software is created. (Nov 2018)
- Passphrase generator is published.
Research Topics
(1) Software Quality Assurance for Artificial Intelligence and Cyber-Physical Systems
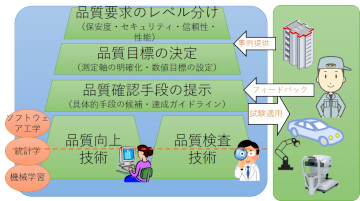
We work on quality assurance process and related software engineering technologies (testing, analysis, verification etc.) for the contemporary software technologies, especially those using a data-driven automatic code-generation (i.e. machine-learning / artificial intelligence) or probabilistic (randomized, non-deterministic) executions. We will find out how these kinds of software can be ensured a high level of reliability and fitted in the existing requirements and processes for software security and safety managements.
(2) Trustworthiness Architecture for near-future CPS Infrastructure
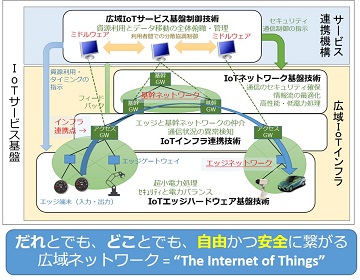
Evolution of “Internet of Things” (IoT) brings us much closer connection between the physical and the “cyber” world. Some expects more than one trillion sensors will be around the connected world in 2030. However, we concern that the current design of the Internet have not enough agility, flexibility, and strength on the aspect of security and management to accommodate such huge numbers of nodes.
We are designing a near-future architecture of the Internet, which will provide better security, privacy and flexibility to its users, still preserving open nature of the Internet.
→ Doormen Project [in preparation]
(3) Safe Execution of Computer Programs
These days, security holes caused by program bugs introduces critical situations such as information leakage (e.g. credit card numbers) or service interruptions. I am currently working on safe execution methods of programs.
Especially, I constructed the Fail-Safe ANSI C Compiler, which prevents all kinds of memory-corruption attacks (such as buffer overrun exploits) for full ANSI C90 language.
(4) Safety of Web application and network protocols
Protocols, implementations of the protocols, or the implementation of the application on the Internet often contain many bugs or defects, which sometimes cause security vulnerabilities. We analyze such vulnerabilities, report those to the developers, and tries to summarize the fundamental and effective approaches to prevent such vulnerabilities.
![[DigiARC]](data/DigiARC-E0-105.png)
![[AIST]](data/symbolaist120x22lg.gif)